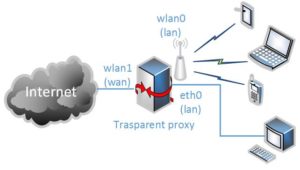
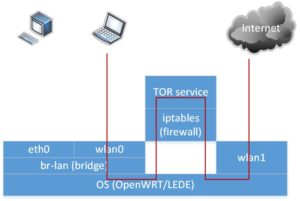
In some public places we want to connect to the Internet without someone watching us. It can be local provider, hotel personnel or something else. With Tor, we can build small machine acting as transparent proxy for simple services as browsing, emails, chatting. In my case, I will use WRAP board with two WiFi cards and OpenWRT/LEDE operating system inside.
In some public places we want to connect to the Internet without someone watching us. It can be local provider, hotel personnel or something else. With Tor, we can build small machine acting as transparent proxy for simple services as browsing, emails, chatting. In my case, I will use WRAP board with two WiFi cards and OpenWRT/LEDE operating system inside.
There is only one prerequisite: connection hidden to the „first mile of internet“. No dark web, no hacking, … Only privacy.
Limitations: no UDP, limited access to some services. If you don’t know, how Tor works, please study.
About WRAP board, OpenWRT/LEDE and also Tor project you can read at my pages:
Building OpenWRT
OpenWRT at Mikrotik Routerboard 512
Rescue of the PC Engines WRAP 2C
PC Engines WRAP 2 memory upgrade
Hidden Services for Tor
Technical details
Hardware
- PC Engines WRAP board with two WiFi cards, one 100 Mbps Ethernet RJ-45 connector and one serial port (RS-232).
- Two compatible WiFi cards (mini PCI) – Atheros.
You can also use any other piece of hardware, which has similar properties.
Software
- Operating system: OpenWRT/LEDE (or any other GNU/Linux) with iptables, odhcpd, dropbear, hostapd, wpa_supplicant, udhcpc, dnsmasq.
- Tor project service.
Final configuration
Black box with WiFi connection to the internet (WAN) over second WiFi card (wlan1). First WiFi card (wlan0) and Ethernet port (eth0) are bridged as br-lan and are used for client access. So it’s possible also to connect a local computer through the Ethernet port.
How it works
Simply, data packets from clients are redirected to Tor, encapsulated, encrypted and transferred over network.
First use on the site:
- System boots;
- auto start wlan0 and eth0;
- auto start DHCP server on br-lan interface (bridge – eth0 and wlan0); now it is possible to connect via WiFi or Ethernet, but there is no internet access;
- the client use ssh client to access the box as root;
- client configure internet access through wlan1 and reboot the box;
- done.
Now, we can use our black box for private surfing.
Configuration
System
At first, please set password for root account.
It’s necessary to configure system parameters. The Tor service needs precise time, so, the first thing is – configuration of NTP servers:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
config system option hostname anongw-my option timezone 'CET-1CEST,M3.5.0,M10.5.0/3' option zonename 'Europe/Prague' option conloglevel '8' option cronloglevel '8' option log_size '64' config timeserver ntp list server pool.ntp.org list server 129.6.15.28 list server 24.56.178.140 list server 81.168.77.149 list server 192.12.19.20 list server 131.215.239.14 option enabled 1 option enable_server 1 config rngd option enabled '0' option device '/dev/urandom' |
Network
Network parameters specifies mainly network type and IP address:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
config interface 'loopback' option ifname 'lo' option proto 'static' option ipaddr '127.0.0.1' option netmask '255.0.0.0' config globals 'globals' # option ula_prefix 'fdc2:0405:e04e::/48' config interface 'lan' option type 'bridge' option proto 'static' option ifname eth0 option ipaddr '192.168.164.1' option netmask '255.255.255.0' # option ip6assign '64' option ipv6 '0' config interface 'wan' option proto 'dhcp' # option proto 'static' option ifname wlan1 option ipaddr '192.168.1.10' option gateway '192.168.1.1' option netmask '255.255.255.0' option dns '8.8.8.8 193.29.206.206' option ipv6 '0' |
Our clients will have IP addresses from range 192.168.164.0/24 – delivered by DHCP.
For internet access we can define own static configuration or dynamic over DHCP. This information we have from our provider.
DHCP server
Here we configure assigning of IP addresses to our clients (lan):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
config dnsmasq option domainneeded '1' option boguspriv '1' option filterwin2k '0' option localise_queries '1' option rebind_protection '1' option rebind_localhost '1' option local '/lan/' option domain 'lan' option expandhosts '1' option nonegcache '0' option authoritative '1' option readethers '1' option leasefile '/tmp/dhcp.leases' option resolvfile '/tmp/resolv.conf.auto' option localservice '1' option port 0 option server '//8.8.8.8' config dhcp 'lan' option interface 'lan' option start '100' option limit '150' option leasetime '12h' config dhcp 'wan' option interface 'wan' option ignore '1' config odhcpd 'odhcpd' option maindhcp '0' option leasefile '/tmp/hosts/odhcpd' option leasetrigger '/usr/sbin/odhcpd-update' |
Wireless
Defines access to our box. The wifi-iface for radio0 defines client access (lan), wifi-iface for radio1 defines access to the internet (wan).
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
config wifi-device radio0 option type mac80211 option channel 8 option hwmode 11g option path 'pci0000:00/0000:00:0d.0' option htmode option txpower '23' option country 'CZ' # option noscan '1' option disabled 0 config wifi-iface option device radio0 option network lan option mode ap option ssid mynetwork option encryption 'psk2' option key 'p4s5w0rd' option macaddr '00:3d:b3:92:3b:da' config wifi-device radio1 option type mac80211 option channel auto option hwmode 11g option path 'pci0000:00/0000:00:11.0' option htmode option disabled 0 config wifi-iface option device radio1 option network wan option mode sta option encryption psk2 option ssid hotel option key h8mcjsc option macaddr '00:4b:b3:93:f2:f4' |
Firewall
Now, we have to redirect data flow through Tor, except SSH. We need SSH for configuring of our box for the first time and later maintenance. But the SSH can be a problem, if we want use it for configuring another computers in the internet. In this case, you can simply modify the appropriate configuration.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
iptables -F iptables -t nat -F iptables -t nat -A PREROUTING -i br-lan -p udp --dport 53 -j REDIRECT --to-ports 53 iptables -t nat -A PREROUTING -i br-lan -p tcp --syn \! --dport 22 -j REDIRECT --to-ports 9040 iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -o wlan1 -m owner --uid-owner 52 -j ACCEPT iptables -A OUTPUT -o wlan1 -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A INPUT -i wlan1 -j DROP |
Tor
This is crucial configuration for Tor service:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
VirtualAddrNetworkIPv4 10.192.0.0/10 AutomapHostsOnResolve 1 AutomapHostsSuffixes .onion,.exit TransPort 9040 TransListenAddress 0.0.0.0 DNSPort 53 DNSListenAddress 0.0.0.0 User tor Log notice syslog DataDirectory /var/run/tor #HiddenServiceDir /etc/tor/hidden_service/ssh #HiddenServicePort 8022 127.0.0.1:22 |
All parameters you can found on Tor project pages.
At the end of the file is configuration of hidden service. If you can use it (if not, please ignore), uncomment these lines and create appropriate directories:
|
1 2 |
root@anongw-my:/#mkdir -m 0700 -p /etc/tor/hidden_service/ssh root@anongw-my:/#chown -R tor:tor /etc/tor/hidden_service/ssh |
After Tor restart, we can found file /etc/tor/hidden_service/ssh/hostname with hostname of the hidden service.
Last words
Now, we have configured Tor transparent proxy on our back box. But this isn’t VPN, our privacy can be compromised on the other side of Tor network.